221.236.12.33 四川省成都市 电信
这位hacker用中国人常用的login 和 password作测试。但是由于我的passw ...
角色 發表於 2010-9-6 08:36


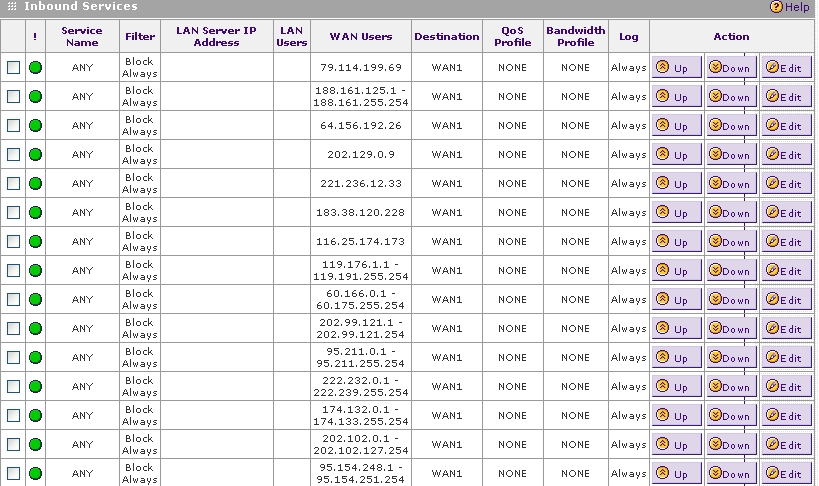
The Hackers' IP ranges that I experienced or through the members here are as below:In view of above ...
bubblestar 發表於 2011-1-19 15:32



| 歡迎光臨 電訊茶室 (http://telecom-cafe.com/forum/) | Powered by Discuz! 7.2 |